Introduction to Ransomware Threats in Virtual Environments
In recent years, ransomware attacks have evolved significantly, targeting not only individual systems but also entire networks and virtual environments. One of the most alarming trends is the exploitation of vulnerabilities in hypervisors, particularly the ESXi platform by VMware. This article delves into how ransomware gangs are leveraging a specific ESXi bug to achieve instant mass encryption of virtual machines (VMs), the implications of such attacks, and strategies for mitigation.
Understanding the ESXi Vulnerability
What is ESXi?
VMware ESXi is a hypervisor that enables the virtualization of physical servers, allowing multiple VMs to run on a single hardware platform. This technology is widely used in enterprise environments for its efficiency and scalability.
The Specific Bug
Recent reports have highlighted a critical vulnerability in ESXi that allows attackers to gain unauthorized access to the hypervisor. This bug can be exploited to execute arbitrary code, leading to the potential for mass encryption of all VMs hosted on the affected server. The ease of exploitation and the devastating impact of such attacks make this vulnerability particularly concerning.
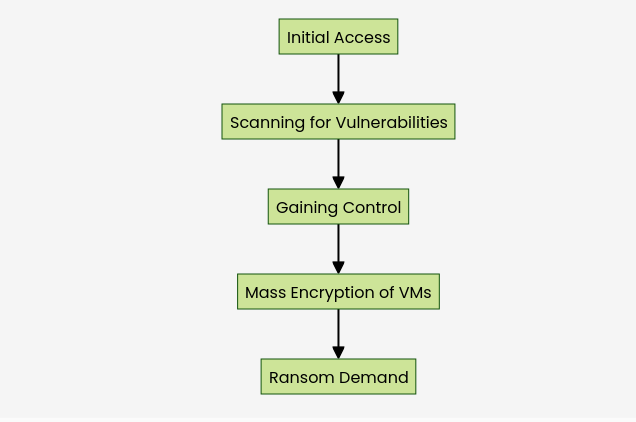
Mechanism of Attack
Initial Access
Ransomware gangs typically gain initial access through phishing attacks, exploiting weak passwords, or leveraging other vulnerabilities in the network. Once inside, they can scan for ESXi servers and identify those that are vulnerable.
Exploitation Process
- Scanning for Vulnerabilities: Attackers use automated tools to identify ESXi servers with the known vulnerability.
- Gaining Control: By exploiting the bug, they can execute commands on the hypervisor, allowing them to manipulate the VMs.
- Mass Encryption: The attackers deploy ransomware that encrypts all VMs in a matter of minutes, rendering critical business operations inoperable.
Diagram: Attack Flow
Implications of Ransomware Attacks on ESXi
Business Disruption
The immediate impact of a successful ransomware attack on ESXi is the disruption of business operations. Organizations may face downtime, loss of access to critical data, and potential financial losses.
Data Loss and Recovery Challenges
In many cases, organizations may not have adequate backups or may find that their backups are also encrypted. This complicates recovery efforts and can lead to permanent data loss.
Reputational Damage
Beyond financial implications, organizations may suffer reputational damage as clients and partners lose trust in their ability to protect sensitive information.
Mitigation Strategies
Regular Patching and Updates
Organizations must prioritize regular updates and patches for their ESXi servers. Keeping the hypervisor up to date can significantly reduce the risk of exploitation.
Network Segmentation
Implementing network segmentation can limit the spread of ransomware. By isolating critical systems, organizations can contain potential breaches and protect sensitive data.
Robust Backup Solutions
Regularly backing up VMs and ensuring that backups are stored offline can provide a safety net in the event of an attack. Organizations should test their backup and recovery processes to ensure they are effective.
Employee Training and Awareness
Educating employees about the risks of phishing and other social engineering tactics can help prevent initial access points for attackers. Regular training sessions can enhance overall security awareness.
Conclusion
The exploitation of the ESXi bug by ransomware gangs poses a significant threat to organizations relying on virtual environments. By understanding the mechanics of these attacks and implementing robust security measures, businesses can protect themselves from the devastating consequences of ransomware. Proactive strategies, including regular updates, network segmentation, and employee training, are essential in safeguarding against these evolving threats.
